ATTACKIQ INC.
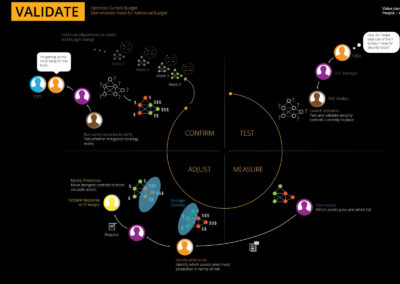
Continuous Validation
As the Director of Product Design and User Experience at AttackIQ, I was a transformative force in the cybersecurity sector, leading the company’s cloud and enterprise subscription-based product strategy. My role was a unique blend of technical acumen and creative brilliance, setting new industry standards for security control and infrastructure.
Goal #1
ATTACKIQ
Automate, Validate, Secure: Revolutionizing Cybersecurity

AttackIQ is a pioneering cybersecurity company that offers a Security Optimization Platform designed to enhance threat-informed defense across organizations. Utilizing the MITRE ATT&CK framework, the platform provides various testing experiences tailored to different organizational needs. It aims to revolutionize security control and infrastructure norms by offering automated validation platforms that balance innovation with user expectations. With a focus on efficiency, effectiveness, and customer-centricity, AttackIQ is setting new standards in the cybersecurity industry.
Goal
The primary aim was to create a comprehensive Security Optimization Platform that would redefine the cybersecurity industry. The focus was on integrating user-centric design principles to ensure a seamless experience across various platforms. Another key goal was to introduce automated validation mechanisms that would revolutionize security control and infrastructure.
Challenge
The journey was fraught with challenges, including the technical complexity of balancing cybersecurity intricacies with user-friendly design. Resource allocation was another hurdle, as building a competent design team from scratch required meticulous planning and management. Additionally, challenging and transforming existing industry norms and practices in security control and infrastructure was no small feat.
Approach
I spearheaded the development of the AttackIQ Platform, starting with in-depth market research to identify industry needs. I then focused on user-centric design and automated validation to meet industry standards. Alongside this, I crafted a strategic roadmap aligned with our long-term goals and conducted ongoing usability tests for continual improvement.
My Role
-
Market Research: Initiated the project with comprehensive research to identify industry gaps and user needs.
-
Design Leadership: Spearheaded the design phase, focusing on user-centric principles to create compelling visuals and seamless interactions.
-
Automated Validation: Implemented automated mechanisms to ensure our security controls met both industry standards and user expectations.
-
Strategic Roadmap: Developed a strategic roadmap to guide the project, aligning all activities with long-term organizational goals.
-
Usability Testing: Oversaw rigorous testing and made iterative improvements to continually enhance the platform’s effectiveness and user experience.
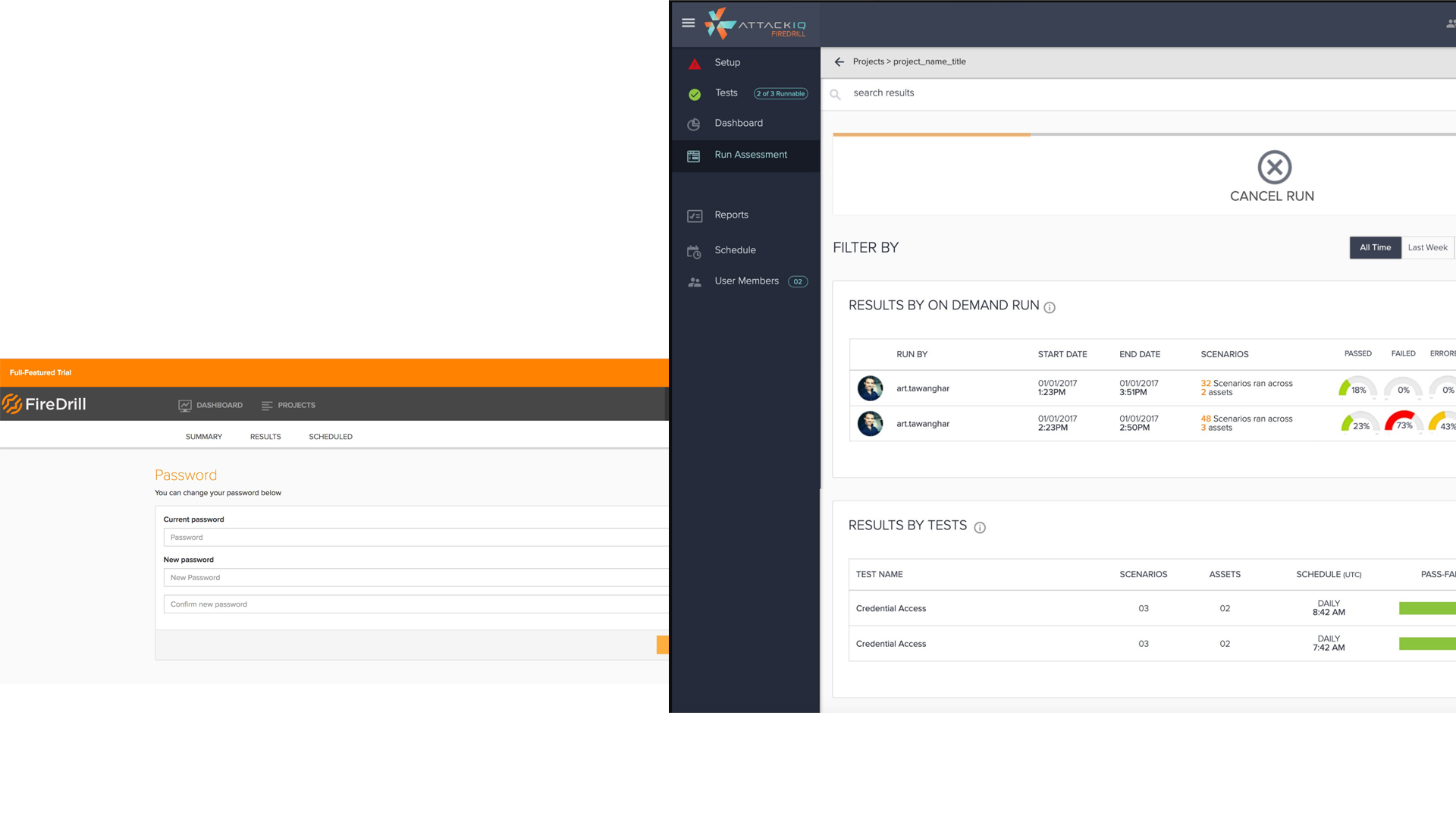
Achievements:
-
Industry Transformation: Successfully revolutionized cybersecurity norms by introducing an automated validation platform, setting a new industry standard.
-
User Experience Excellence: Achieved a seamless user experience across web and mobile platforms, elevating customer satisfaction and engagement.
-
Team Building: Built a high-performing Design team from scratch, curating a group of professionals who shared the vision of blending creativity with strategic design.
-
Efficiency through Agile: Utilized Agile/Lean methodologies to efficiently manage various enterprise SAAS and cloud/subscription services, achieving a balance between user experience and technical capabilities.
-
Customer-Centric Success: Facilitated focus groups and participatory design sessions that led to comprehensive user engagement, resulting in enhanced customer experiences backed by data-driven insights.
-
Technical Mastery: Demonstrated proficiency across a wide range of technologies, contributing to the platform’s robustness and adaptability.
-
Innovative Collaboration: Collaborated seamlessly with cross-functional teams to deliver end-to-end user experiences that were both innovative and user-focused, driving the continual improvement of the platform.
-
Strategic Alignment: Successfully aligned the product vision with long-term organizational goals through a well-crafted strategic roadmap, ensuring sustained growth and innovation.
-
Remarkable ROI Growth: Achieved an astounding 200% gain in Return on Investment (ROI), validating the effectiveness of the platform and contributing to the company’s financial success.
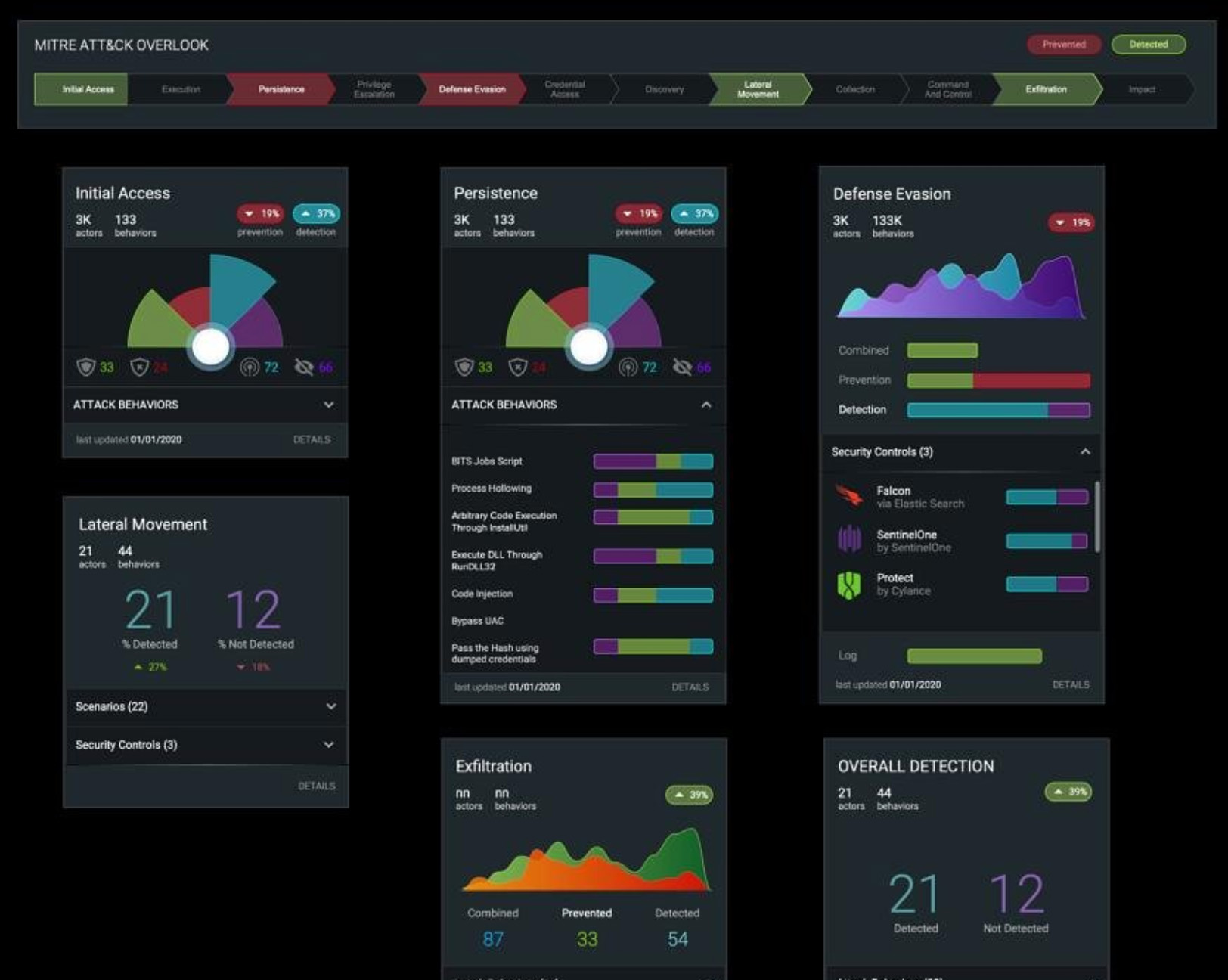
The Approach:
-
Holistic Approach: Adopted a multi-faceted strategy that encompassed market research, user-centric design, automated validation, and strategic road mapping.
-
User Focus: Prioritized user needs and expectations through comprehensive research and user-centric design principles, leading to a highly intuitive and effective platform.
-
Automated Validation: Implemented automated mechanisms for continuous security control validation, ensuring compliance with industry standards and user requirements.
-
Strategic Alignment: Crafted a strategic roadmap that served as the project’s blueprint, aligning all developmental activities with the company’s long-term goals.
-
Quality Assurance: Conducted rigorous usability testing and iterative enhancements to ensure the platform’s effectiveness and user experience met the highest standards.
Strategy:
Phase 1: Research & Planning
- Conducted comprehensive market and user research to identify gaps and needs in the cybersecurity landscape.
- Developed a strategic roadmap to guide the project, aligning it with long-term organizational goals.
Phase 2: Design & Development
- Spearheaded the design phase, focusing on user-centric principles to create compelling visuals and interactions.
- Collaborated with cross-functional teams to develop the platform, ensuring technical robustness and scalability.
Phase 3: Validation & Testing
- Implemented automated validation mechanisms to continuously test the platform’s security controls.
- Conducted rigorous usability testing to ensure the platform met user expectations and industry standards.
Phase 4: Implementation & Deployment
- Rolled out the platform in a staged manner, monitoring for any issues and making iterative improvements.
- Ensured seamless integration with existing systems and compliance with industry regulations.
Phase 5: Monitoring & Optimization
- Continuously monitored the platform’s performance through key performance indicators (KPIs).
- Made iterative enhancements based on user feedback and data analytics, aiming for continual improvement and effectiveness.
Phase 6: ROI Analysis & Scaling
- Conducted a thorough ROI analysis, which showed a remarkable 200% gain, validating the platform’s effectiveness.
- Used the ROI data and user feedback to scale the platform, further enhancing its features and capabilities.
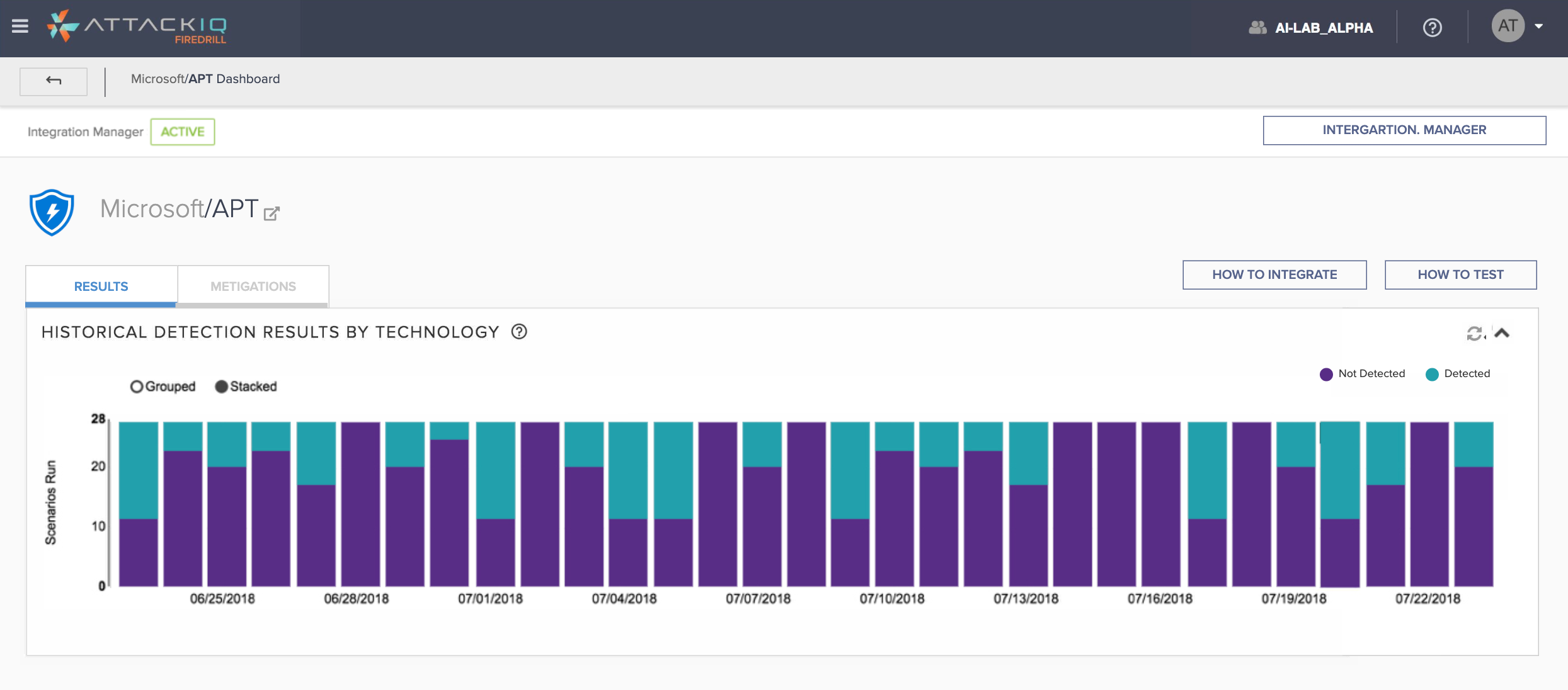
Key Metrics:
Setup Efficiency Metrics
- Time-to-Setup: Measures the speed at which assessments can be set up, indicating the platform’s ease of use.
Scenario Execution Metrics
- Scenario Run Time: Tracks the time taken to execute desired scenarios, assessing the platform’s performance efficiency.
- Scenario Success Rate: Measures the percentage of scenarios that run successfully without errors, indicating reliability.
Clarity and Mitigation Metrics
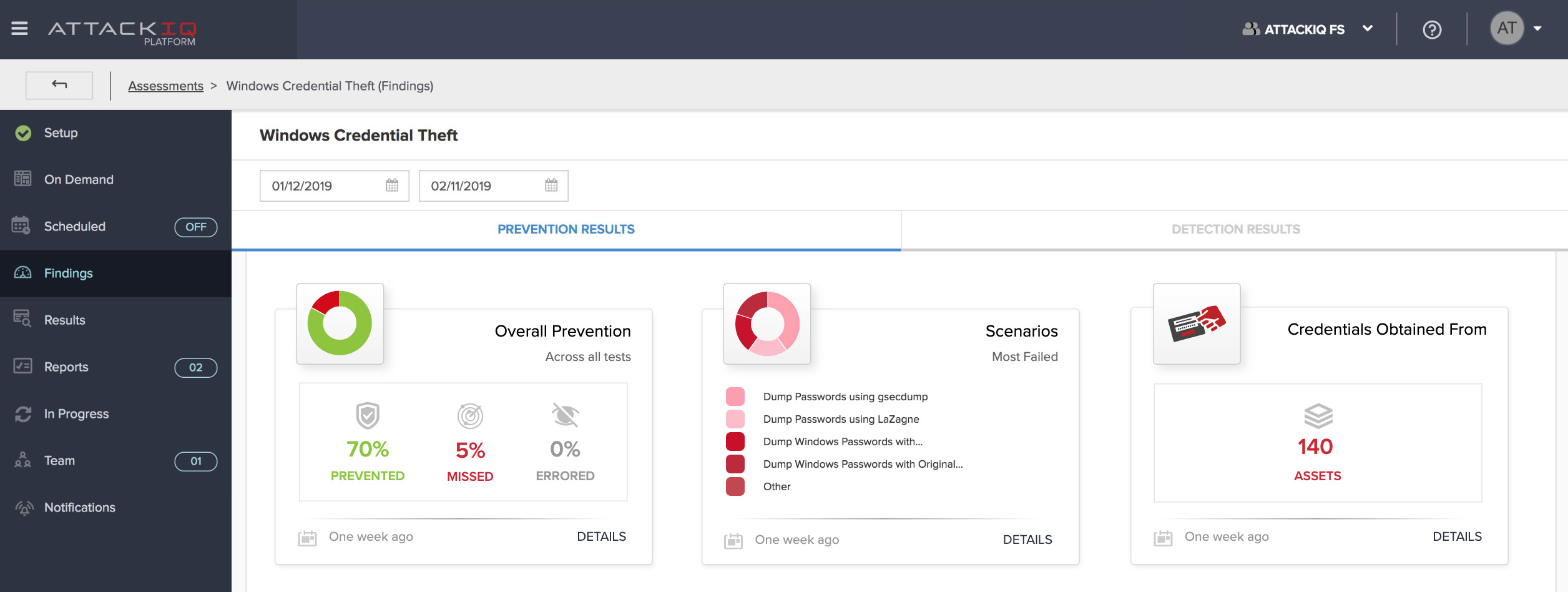
- Findings Clarity Index: A qualitative metric based on user surveys to gauge how clear and understandable the findings are.
- Mitigation Success Rate: Measures the effectiveness of the platform’s recommendations in helping users implement correct mitigation strategies.
Re-Run and Communication Metrics
- Re-Run Efficiency: Tracks the time and effort required to re-run tests, assessing how easily users can iterate on their security setups.
- Operator Communication Index: A qualitative metric based on user feedback to evaluate the effectiveness of communication between the platform and the operator.
Issue Resolution Metrics
- Time-to-Resolution: Measures the time taken from identifying an issue to confirming its resolution, indicating the platform’s effectiveness in problem-solving.
These metrics provide a detailed understanding of how well the AttackIQ Platform performs in terms of setup efficiency, scenario execution, clarity of findings, mitigation guidance, and issue resolution. They are crucial for continuous improvement and ensuring user satisfaction.
Key Learnings and Takeaways:
Importance of User-Centric Design
- Understanding that a focus on user needs and expectations is crucial for the platform’s success. This approach led to higher user engagement and satisfaction.
Value of Automated Validation
- Learning that automated validation not only improves efficiency but also ensures that the platform meets industry standards, thereby gaining user trust.
Necessity of Clear Communication
- Realizing the importance of clear and effective communication between the platform and the operator, especially for issue resolution and mitigation guidance.
Agility and Flexibility
- Recognizing the value of Agile methodologies in managing a complex project, allowing for quick iterations and adaptability to change.
Financial Viability
- The remarkable 200% ROI gain validated the financial viability of the platform, emphasizing the importance of aligning the product with both user needs and business goals.
Continuous Improvement
- Understanding that the platform’s development is an ongoing process. The key metrics served as invaluable tools for continuous improvement and informed decision-making.
Team Synergy
- Learning that building a cohesive and skilled team is essential for the successful execution of a complex project. Team alignment with the project’s goals was a significant factor in its success.
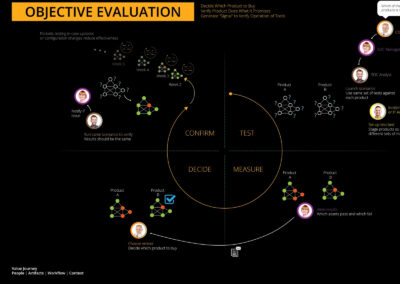
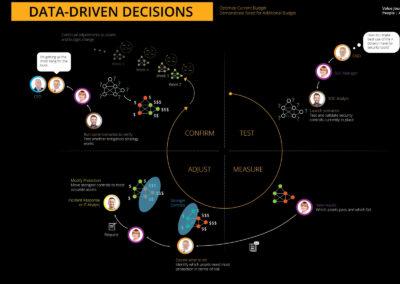
Data-Driven Decision Making
- Realizing the importance of using key metrics and data analytics for making informed decisions, ensuring that the platform remains effective and continues to meet user needs.
These learnings and takeaways have been instrumental in shaping the platform and will continue to guide future strategies and improvements.
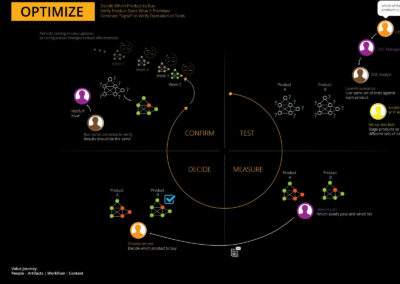
Optimization:
Optimization is a fundamental aspect of AttackIQ’s operational strategy, focused on elevating both user experience and overall platform performance. Here’s our approach to optimization:
User Experience (UX) Optimization
- Goal: To craft an intuitive, user-friendly interface that caters to both security analysts and end-users.
- Strategy: Leverage A/B testing, user feedback, and data analytics to continually refine the UX design.
Workflow Efficiency
- Goal: To optimize the workflow for security analysts, particularly emphasizing quick and accurate threat assessments.
- Strategy: Utilize real-time analytics and key performance indicators to pinpoint bottlenecks and areas for improvement.
Resource Utilization
- Goal: To maximize the efficient use of both human and technological resources.
- Strategy: Employ data analytics to guide resource allocation, ensuring peak productivity and cost-effectiveness.
Compliance and Quality Assurance
- Goal: To guarantee that all features and functionalities comply with cybersecurity regulations.
- Strategy: Integrate compliance checks into the development and testing phases, using data to monitor and ensure compliance.
Scalability
- Goal: To develop a platform that can effortlessly adapt to growing user numbers and additional features.
- Strategy: Implement modular architecture and cloud-based solutions to ensure seamless scalability.
Data-Driven Decision Making
- Goal: To make decisions that are aligned with user needs and business goals.
- Strategy: Establish a robust data analytics framework that offers actionable insights for decision-making.
Accessibility
- Goal: To make the platform accessible to a broad audience, including those with disabilities.
- Strategy: Include accessibility features and conduct regular audits to ensure compliance with accessibility standards.
ROI Maximization
- Goal: To achieve the highest possible return on investment for all stakeholders.
- Strategy: Continuously measure key performance indicators against set objectives and adapt strategies as needed.
Through these optimization strategies, AttackIQ aims to create a platform that is not only efficient and user-friendly but also scalable and compliant with cybersecurity regulations. This comprehensive approach to optimization is crucial to AttackIQ’s mission of revolutionizing the cybersecurity landscape.
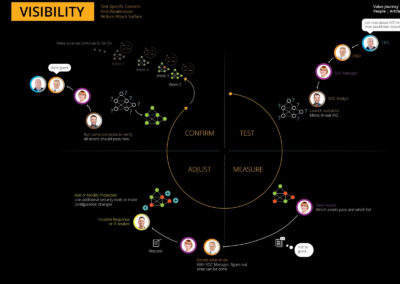
Visibility:
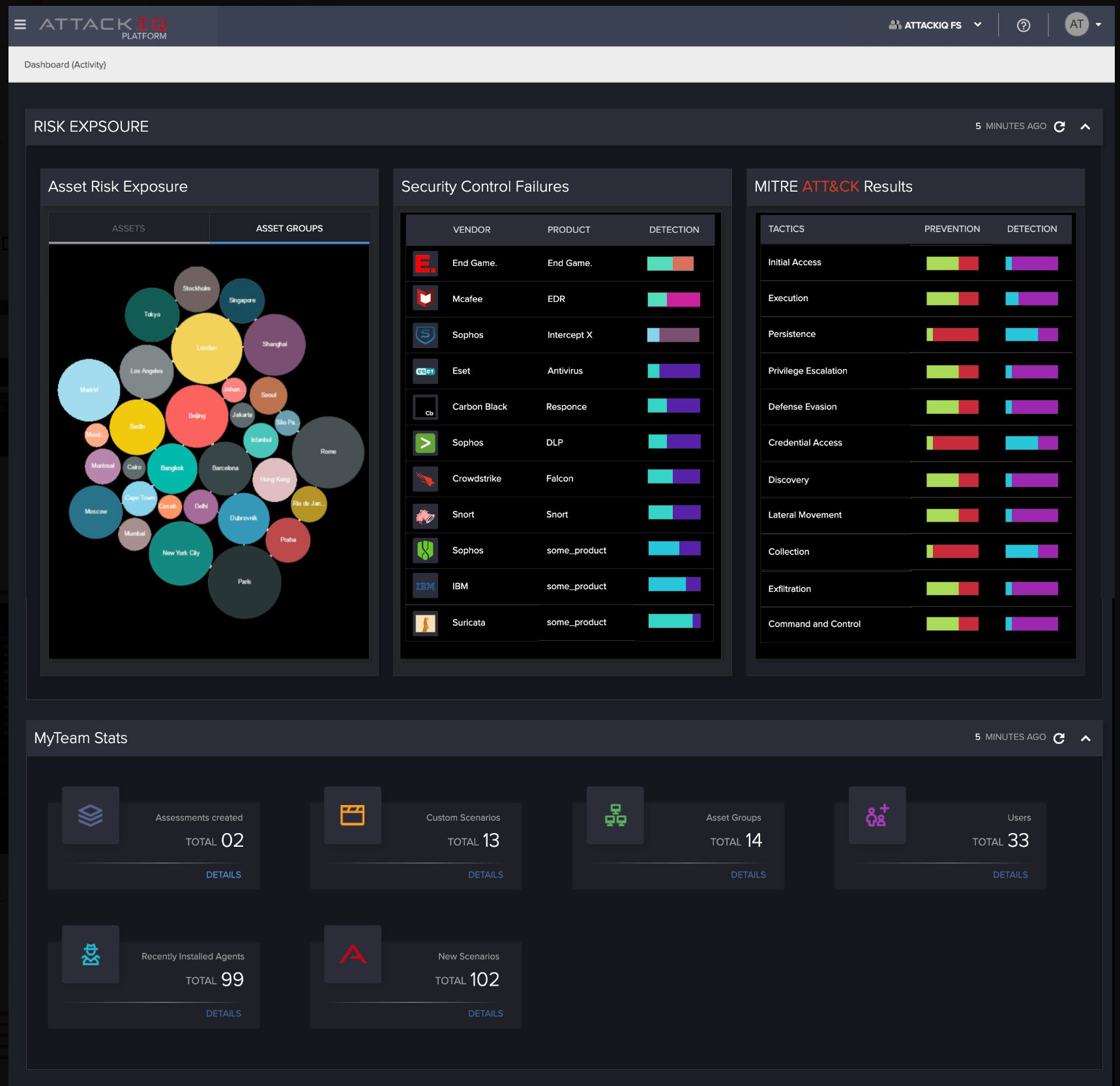
Visibility is a key component of AttackIQ’s operational philosophy, ensuring that all stakeholders have immediate access to crucial data and insights. This transparency builds trust, fosters collaboration, and facilitates rapid decision-making. Through dashboards and real-time analytics, security analysts can monitor key metrics like threat assessments, validations, and resolutions, thereby optimizing workflow. Stakeholders and investors are also kept informed with regular reports and updates, ensuring alignment with business objectives. Overall, enhanced visibility contributes to AttackIQ’s commitment to accountability, efficiency, and data-driven optimization.
Iterations:
Iterations are central to AttackIQ’s methodology for ongoing improvement. We employ a cycle of prototype testing, feature releases, and workflow optimization to refine our platform. Each iteration is informed by real-world data, user feedback, and key performance metrics. This enables us to make educated adjustments, whether it’s improving user experience, ensuring compliance, or preparing for scalability. Through this iterative process, AttackIQ remains agile, user-focused, and aligned with business objectives, setting us apart in the cybersecurity industry.
Next Steps:
Phase 1: Data Analysis and Feedback Collection
- Conduct a comprehensive review of the key metrics and user feedback to identify areas for improvement and potential new features.
Phase 2: Strategic Planning
- Update the strategic roadmap based on the data analysis and feedback, setting new milestones and objectives for the next quarters.
Phase 3: Resource Allocation
- Determine the resources needed for the next phases, including manpower, technology, and budget, and allocate them accordingly.
Phase 4: Development and Testing
- Initiate the development of new features and improvements identified in the strategic planning phase.
- Conduct iterative testing to ensure these updates meet quality and compliance standards.
Phase 5: User Training and Documentation
- Update user manuals, FAQs, and training materials to reflect the new features and improvements.
- Conduct training sessions for both internal teams and end-users to ensure smooth adoption of the updates.
Phase 6: Soft Launch
- Roll out the new features and improvements to a smaller user base for real-world testing and to gather initial feedback.
Phase 7: Full-Scale Deployment
- After successful testing and any necessary adjustments, deploy the updates to the entire user base.
Phase 8: Monitoring and Optimization
- Continuously monitor key performance indicators and user feedback to assess the impact of the new features and improvements.
- Make any necessary optimizations based on this data.
Phase 9: Stakeholder Communication
- Keep stakeholders, including investors and partners, informed about the updates and their impact through regular reports and meetings.
Phase 10: Future Planning
- Begin planning for the next cycle of updates, informed by the data and feedback from the recent deployment.
By following these next steps, AttackIQ aims to continue its trajectory of innovation and excellence, further solidifying its position as a leader in the cybersecurity industry.